 |
|
 |
 |
 |
| Our Secure Grid Filesystem has been developed based on two core building-block
technologies. One is
SFS (Self-certifying File System),
the other is
GSI (Grid Security infrastructure).
The former technology is being developed by the
research group led by A/Prof. David Mazières and is a filesystem offering
some features of much interest. The most promising feature brought by the
filesystem for Bio-related research is data confidentiality, meaning the data
in transit on the net is encrypted. The latter is a de facto standard
security infrastructure, which was developed by
Globus Project, for the Grid. The outstanding and promising feature delivered by the
technology is single sign-on functionality. It allows us to freely utilize
the computational resources such as processors and data storages on the
Grid, just by typing our own passphrase as a credential of user identity
once. |
|
| To satisfy the five demands from Bio-related researchers, we combine the
two key technologies without losing the promising functionalities in both
two technologies. More specifically, we aim to build a secure grid filesystem
that allows us to dynamically mount multiple filesystems located on the
remote sites after single sign-on authentication. The Secure Grid Filesystem
that as a result can be embodied is so convenient. |
 |
| We implemented a prototype by creating
GSI server (GSI-SFS Key Server) and client (GSI-SFS Key Client)
dependent from SFS. The whole system including GSI, SFS
and GSI-SFS Key Server/Client is named GSI-SFS.
|
|
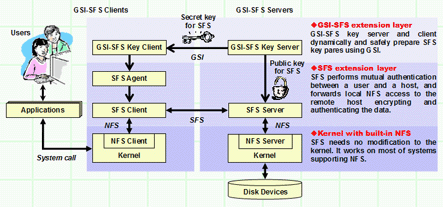 |
| Figure: The structure of GSI-SFS |
|
| GSI-SFS consists of three layers: GSI-SFS extension layer, SFS extension
layer and NFS layer. NFS is the most popular network filesystem supported
in many UNIX systems. Because the lowest layer of GSI-SFS is NFS, GSI-SFS
works on many systems supporting NFS. SFS is a secure network filesystem
based on NFS, and SFS extends NFS to a global filesystem. SFS authenticates
a user and a host each other with their public keys. After successful authentication,
SFS forwards local NFS access to remote encrypting and authenticating all
data transfered through network. |
|
| SFS's public key authentication method works well in small storage sharing,
but it comes to a problem when the method is used on the Grid. It is because
there are a number of users and hosts in the Grid environment. That means
all Grid users have to register their public keys to all hosts they use.
Users have to put their public keys securely (without being altered) to
every host, and also get host IDs from every host securely. For these reasons,
using SFS is considered very difficult in Grid environmet. |
|
| To solve the problem previously described, we implemented GSI-SFS Key Server
(gsisfskeyd) and Client (gsisfskey). They automate the key registration
securely with GSI. The authentication sequence is as follows. |
|
- When authentication is required, SFS Agent (sfsagent) invokes gsisfskey.
- gsisfskey connects to gsisfskeyd, then they authenticate mutually by GSI.
- After successful authentication, gsisfskeyd generates new user key pair.
- gsisfskeyd registers the public key to SFS Server.
- gsisfskeyd sends the secret key, the host ID and the location of home directory to gsisfskey with encryption and authentication of GSI.
- gsisfskey registers received secret key to sfsagent.
- gsisfskey informs the host ID and the home directory to sfsagent.
|
 |
GSI-SFS requires following software properly installed and set on your system. Since current GSI-SFS uses /etc/passwd to determine user's home directories, SFS should export user's home directories same as path as /etc/passwd. This should be improved in future versions.
- Operating system supporting NFS3
- GSI of Globus Toolkit >= 2.0
- SFS 0.7.2 or compatible
- C Compiler (We don't distribute binary packages.)
|
|
| GSI-SFS is developed and tested on following system.
|
|
| When you try on the different system, please tell me whether it works or not. |
 |
Downloading the software is limited to registered people only.
If you want to download them, please register first.
You will receive a password for downloading within a couple of days.
|
 |
Expand the archive downloaded above, and chdir to the extracted directory.
•Example:
$ tar xvfj gsisfskey-x.x.x.tar.bz2
$ cd gsisfskey-x.x.x |
|
| GSI-SFS Key Server/Client support Autotools. You can build and install in the configure-make-make install manner. |
|
| To specify install options and generate a Makefile, run the `configure' script. The script needs the directory where Globus Toolkit is installed and the flavor which was specified at the Globus installation. The important options are as follows: |
| Option |
Comment |
Default |
| --prefix |
Prefix where GSI-SFS Key is installed |
/usr/local |
| --enable-ipv6 |
Enable IPv6 support |
disabled |
| --with-globus-prefix |
Prefix where Globus is installed |
$GLOBUS_LOCATION |
| --with-globus-flavor |
Flavor of Globus Toolkit |
$GLOBUS_FLAVOR |
•Example:
$ ./configure --prefix=$GLOBUS_LOCATION --with-globus-flavor=gcc32dbg
|
|
Next, "make" and "make install".
•Example
$ make
$ su
# make install
|
|
You can also build and install with RPM (RPM Package Manager). It requires $GLOBUS_LOCATION and $GLOBUS_FLAVOR are set.
•Example ($GLOBUS_LOCATION has been set as an environment variable)
# GLOBUS_FLAVOR=gcc32dbg rpmbuild -tb gsisfskey-x.x.x.tar.gz
# rpm -Uvh /usr/src/redhat/RPMS/i386/gsisfskey-x.x.x.i386.rpm
# rpm -Uvh /usr/src/redhat/RPMS/i386/gsisfskey-server-x.x.x.i386.rpm
|
 |
To start GSI-SFS Key Server, simply run gsisfskeyd. Currently, the server doesn't use any configuration file.You must specify all required options from command - line. To get the complete list of options, run the command with a "--help" option.
•Example
# gsisfskeyd --help
# gsisfskeyd &
|
|
If your system has initscripts and chkconfig, you can use the startup script included in the archive. As it has hard-coded paths and options, you may need to modify it.
•Example
# cp gsisfskeyd.init /etc/init.d/gsisfskeyd
# cd /etc/init.d
# vi gsisfskeyd (customize suitable for your system)
# chkconfig --add gsisfskeyd
# service gsisfskeyd start
|
|
The server listens on TCP port 2657. Check if it is listening.
•Example
# netstat -lt (for Linux system)
....
tcp6 0 0 *:2657 *:* LISTEN
....
|
| When you try on the different system, please tell me whether it works or not. |
 |
| Confirm SFS client (sfscd) is running. GSI-SFS Key Client (gsisfskey) needs no configuration. |
 |
This section presumes the following situation:
- GSI, NFS, SFS, and GSI-SFS Server are set up on a server host.
- GSI, NFS, SFS, and GSI-SFS Client are set up on another client host. (Because of SFS specification, the server and client MUST NOT on the same host.)
- You are logging on the client.
|
|
First, activate your GSI proxy.
•Example
$ grid-proxy-init (and enter your passphrase) |
|
To prepare SFS keys manually, use gsisfskey command. You can get option list with --help option.
•Example
$ gsisfskey --help |
|
According to the following example, a user creates a symbolic link pointing a root directory exported on the remote SFS server.
•Example
$ gsisfskey --symlink gsisfsserv.myorganization.org
$ cd gsisfsserv.myorganization.org |
|
To automate SFS key registration, use gsisfskey as SFS certprog.
•Example
$ gsisfskey --initiate
$ cd /sfs/gsi-home/gsisfsserv.myorganization.org |
|
|